Download this Backgrounder as a pdf
Read the panel discussion transcript
After the terrorist attacks of September 11, 2001, exposed numerous weaknesses in the nation’s immigration system, Congress overwhelmingly passed the Enhanced Border Security and Visa Entry Reform Act of 2002, which the president signed in May 2002.1 The visa tracking law, as it is often called, and the USA Patriot Act, were the two primary legislative responses to the attacks. While the USA Patriot Act has been the subject of intense debate, implementation of the visa tracking law has received relatively little attention. This Backgrounder is the first report to systematically examine the implementation of the law so far, and specifically the Bush Administration’s compliance with the deadlines it laid out. We find that, although a number of important reforms were implemented by the mandated deadlines, many others were implemented well after their deadlines passed, and still others have not been implemented at all.
Among the findings:
- Of the 22 mandated deadlines that already have passed, more than half (13) were missed.
- Of those 13 deadlines that were missed, four of the required reforms eventually were implemented, while nine others still have not been implemented as of this writing.
- One of the most important missed deadlines is the Administration’s failure to report any progress on the development of an integrated biometric-based database, dubbed Chimera, that would give the State Department and the Department of Homeland Security real-time access to law enforcement, immigration, and intelligence information on every alien who seeks admission to the United States. The Administration has failed even to establish the required nine-member commission to oversee the development of Chimera, thus indefinitely stalling any progress on the system.
- The government still is not checking the names of all aliens from "visa waiver" countries against terrorist watch lists at ports of entry, though it was required to do so immediately upon enactment of the visa tracking law. Checking these names is critically important because visa waiver aliens (arrivals from one of 27 countries whose nationals do not require visas to come to the United States as tourists or short-term business visitors) are not vetted by an American consulate overseas prior to their arrival at a U.S. port of entry.
- Machines that can read and compare biometric information on Border Crossing Cards have yet to be installed at most ports of entry along the U.S.-Mexico border, greatly facilitating fraudulent use of the cards.
- Despite significant failures, however, several provisions of the visa tracking law have been successfully implemented, including:
- Creation of an interim data-sharing system that permits relevant government agencies to access data on aliens;
- Development of a biometric technology standard to verify the identity of non-citizens;
- Establishment of terrorist lookout committees in U.S. missions abroad;
- Advance electronic submission of passenger manifests by all commercial airlines and vessels;
- Implementation of the foreign student tracking system (SEVIS);
- Submission to Congress of an annual report on alien absconders who fail to show up for removal following a final order of deportation.
If fully implemented, the visa tracking law could significantly enhance national security by reducing the chances that terrorists would again be able to exploit weaknesses in the nation’s immigration system. Implementation also could help in reducing illegal immigration by making it more difficult for an alien to overstay a temporary visa. However, as we approach the second anniversary of the law’s enactment, the Bush Administration is falling behind and has not carried out several of the legislation’s key provisions. As a result, many of the loopholes that were exploited by the 9/11 terrorists are still open, leaving us vulnerable to future attacks.
Problems Prior to 9/11
In a detailed report published in May 2002, the Center for Immigration Studies documented the various ways al Qaeda terrorists, including the September 11th hijackers, have exploited the nation’s lax immigration system over the past 10 years.2 One of the most important findings of that report was that violations of immigration laws were very common among terrorists. Of the 48 terrorists studied, at least 21 had violated U.S. immigration laws prior to taking part in terrorism, including several of the September 11th terrorists. While others may not technically have violated the law, many gained entry into the country — or continued to operate in the United States — because of the lax way our immigration system is administered. Because violations of immigration laws are so common among terrorists, strict enforcement of immigration law should be considered a key component of our efforts to prevent future terrorist attacks.
Some of the major weaknesses in the nation’s immigration system that have facilitated terrorism in the past include:
- a failure to properly vet visa applicants overseas;
- a lack of information with which to thoroughly screen aliens at ports of entry;
- the absence of a system to track aliens and determine whether visa requirements, including time limits on permission to remain in the United States, are complied with once the alien is in the United States;
- the failure to remove those who do not honor the terms of their visas;
- an inability to determine the true identity of aliens;
- and a lack of information sharing between federal, state, and local agencies.
The visa tracking law was designed to address many of these problems. Equally important, it was designed to send a clear signal that the United States intends to regain control over its borders and to reassert the rule of law in our immigration system.
While the visa tracking law did not address all aspects of our immigration problem — e.g., inadequate resources for border and interior enforcement and inadequate staffing levels at American consulates abroad — the law still represents a critical first step in reducing our vulnerability to future terrorist attacks. Thus, it is necessary to determine the extent to which the Administration successfully has carried out the various requirements in the legislation.
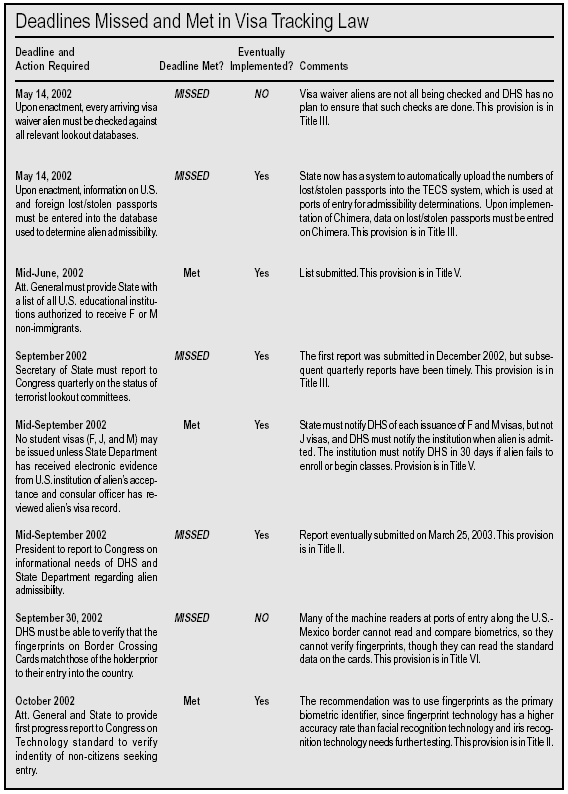
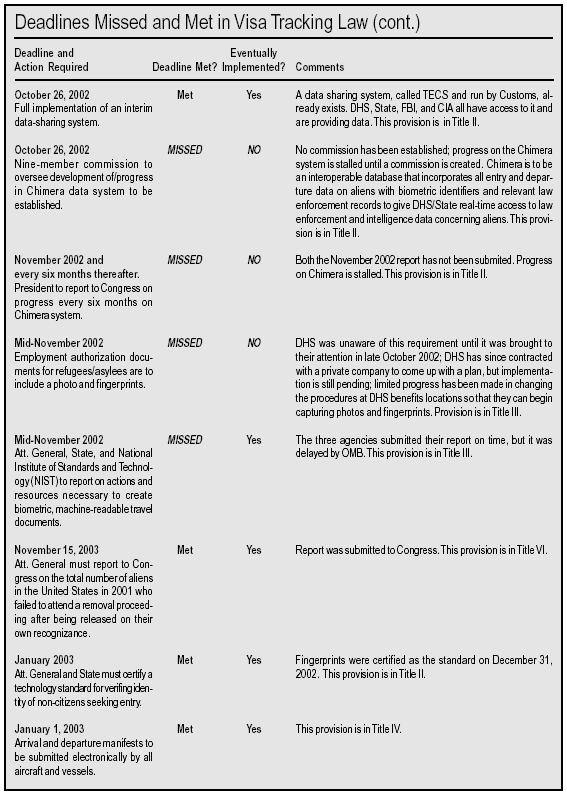
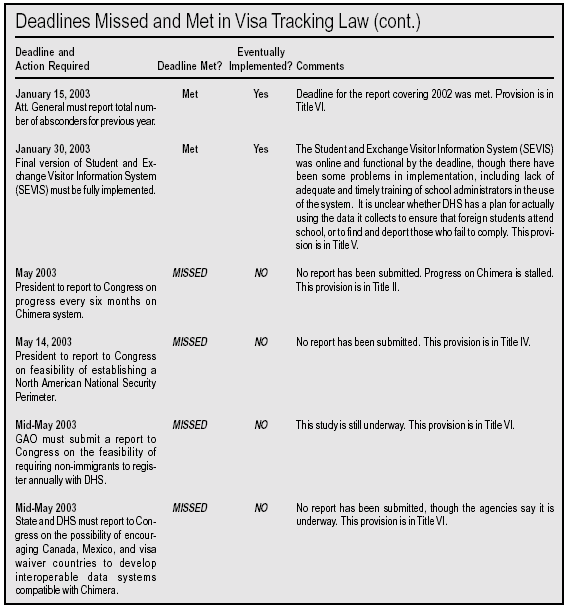
Reading the Chart
The accompanying chart (below) lists (in chronological order of the deadline dates) the 22 reforms required by the Enhanced Border Security and Visa Entry Reform Act to have been implemented by November 2003. The first column describes the action required by the law and lists its mandated implementation deadline. The second column states whether the deadline was met. The third column notes whether the action has been implemented at all yet, i.e. either on time or late. The "Comments" column includes a brief description of each action’s importance and the section of the visa tracking law where the requirement for action can be found. By glancing through the chart the reader can gain a clear sense of the Bush Administration’s progress in meeting the deadlines set by Congress. We summarize below some of the major findings in the chart.
The Failures
Of the 22 deadlines mandated by the visa tracking law, nine of the required reforms have not been implemented at all and four were implemented after the deadlines passed. Given the importance of immigration policy to homeland security, it is disconcerting to see that the Administration has fallen so far behind in implementing these reforms. The most significant of the non-implemented provisions can be divided into three broad areas: document fraud; information sharing; and admission/removal.
Document Fraud. The visa tracking law required that employment authorization documents for refugees and asylees include a photograph and fingerprints by November 2002. This requirement has not yet been met.
Employment authorization documents, which give the holder the legal right to work in the United States, are some of the most sought-after immigration documents. Absent biometric identifiers, employment authorization documents may be easily swapped, sold, or counterfeited. While refugees and asylees do not represent a huge number of people relative to other visa categories, the smaller size of the program should have made it relatively easy to incorporate a photograph and fingerprints on these employment authorization documents. Moreover, the more secure documents could serve as the prototype for work authorization documents for all non-immigrants (aliens granted permission to enter the United States for a particular purpose and limited duration, such as students and guest workers) and for the hundreds of thousands of aliens granted Temporary Protected Status in the United States. The fact that this requirement has not been met is a troubling sign because it suggests that the Administration does not fully appreciate the demand for work authorization documents or the ease with which they are fraudulently used.
The visa tracking law also required the Department of Homeland Security (DHS) to have the ability by September 30, 2002, to verify that the fingerprints on Border Crossing Cards match those of the holder prior to their entry into the United States. Border Crossing Cards permit Mexican nationals to enter the United States for periods of up to 72 hours without having to apply for a visa each time they seek entry. These cards are in high demand among Mexicans who live in border areas or whose business involves routine cross-border activities. The administration has expended significant resources to create and issue secure, machine-readable, biometric Border Crossing Cards to deter fraudulent use and counterfeiting. While DHS has purchased several machines capable of reading standard identification cards, the majority of them are not able to read and compare the digitized fingerprints on the Border Crossing Cards. Without this capability, DHS has no way to ensure that the presenter of the card is the same person to whom it was issued.
Information Sharing. One of the most important reforms required by the visa tracking law is the creation of an integrated data system called Chimera. The Chimera system is supposed to contain biometric identifiers (a photograph and fingerprints), immigration and law enforcement records, and intelligence information on every visa applicant. Chimera is to be used to determine the admissibility and deportability of aliens, since it will include any available evidence of prior immigration violations, criminal records, or terrorist connections.
Prior to September 11, 2001, the Immigration and Naturalization Service (INS) had several separate data systems that were incompatible with one another and with other federal law enforcement agencies, including the Federal Bureau of Investigation (FBI). For example, the INS had separate databases for criminal/illegal aliens, for naturalization applicants, for non-immigrant, and for lawful permanent residents. While there was some data sharing among these systems, there were critical gaps. The data system for criminal/illegal aliens, called IDENT, was the only system that stored an electronic fingerprint and photo, but it was not compatible with the FBI’s criminal database, NCIC. The database for naturalization applicants was incompatible with IDENT, as well, so there were instances of aliens who were in deportation proceedings in one INS District being naturalized by another INS District. The purpose of Chimera is to combine all available data on aliens in one database to which all immigration, law enforcement, and intelligence officers have access. This will allow, for example, a CIA agent who receives intelligence about a suspected terrorist to make that intelligence available to immigration inspectors who can then prevent the alien from gaining admission into the United States.
The lack of communication between federal agencies clearly played a role in facilitating terrorism in the past. Khalid al Midhar, who may have been the pilot on American Airlines flight 77 on September 11th, was identified by the CIA as a terrorist in January 2001. He was permitted to enter the United States in August 2001, however, because the CIA never put his name on the watch lists that should have led an immigration inspector to deny him entry. Chimera would ensure that immigration inspectors have access to CIA intelligence. It also would contain fingerprints of all visa applicants, so a suspected terrorist would have a much more difficult time using a stolen or fraudulent identity to gain admission.
This automated, integrated identification and tracking system for all visa applicants does not guarantee safety from terrorism, but it gives immigration and other law enforcement personnel an essential tool to prevent terrorists from being given legal permission to enter the United States in the first place or to remain in the country if they violate the terms of their visas.
The Administration’s failure to report any progress in creating Chimera and its failure to appoint the nine-member commission required by the visa tracking law to oversee the development of Chimera are perhaps the most significant missed deadlines. Without the Chimera system, there is no permanent, integrated data-sharing system that will allow all law enforcement and intelligence agencies to communicate in real time and to access all available data on non-citizens, including biometric identifiers.
Another area related to information sharing that has not been implemented concerns the failure to report to Congress on the feasibility of establishing a North American National Security Perimeter. The State Department and the Department of Homeland Security have also not reported to Congress on the possibilities for encouraging Canada, Mexico, and visa waiver countries to develop data systems compatible with Chimera.
Admission/Removal. Upon enactment of the visa tracking law, immigration inspectors are required to check every arriving "visa waiver" alien against all relevant terrorist lookout databases before granting the alien admission to the United States. The visa waiver program allows tourists and business travelers from 27 industrial democracies, such those in Western Europe and East Asia, to enter the United States for up to six months without first getting a visa from an American consulate overseas, as is required for almost all other foreign visitors. This means that visa waiver nationals can enter the country without ever having been vetted by an American consulate. It is therefore critically important that, at the very least, their names be checked against the list of known terrorists and criminals at the U.S. port of entry. The fact that this goal still has not been achieved represents a huge weakness in homeland security.
While some may think it unlikely that an al Qaeda terrorist would be a citizen of a visa waiver country, in fact two al Qaeda terrorists born in Western Europe, Zacarias Moussaoui and Richard Reid, already have used the visa waiver program to gain admission to the United States. Moussaoui, suspected of being the 20th September 11th hijacker, was born in France and Reid, the so-called "shoe bomber," was born in Great Britain. Moreover, the attacks of September 11th were planned largely in Western Europe. Foreign terrorists already have demonstrated a sophisticated understanding of U.S. immigration law and a willingness to exploit weaknesses in it. The failure to check every visa waiver alien at U.S. ports of entry is an opening terrorists likely will exploit again if it is not closed.
DHS’s inability to verify that the fingerprints on Border Crossing Cards match those of the holder prior to admission, mentioned above in the section on document fraud, also presents a major weakness in admission and removal procedures. Without the equipment to compare the fingerprints on the cards with the aliens’ fingerprints, authorities cannot verify that the cards are being used by the person to whom they were issued, creating an opportunity for fraudulent entry. In fact, there is anecdotal evidence that the cards are being used by smugglers to get their clients into the United States. Once the clients gain entry into the United States, the smugglers then collect the cards and return to Mexico, where they either give them back to their legitimate owners or use them again for another group of illegal aliens. Besides greatly facilitating illegal immigration, there is every reason to believe that if other means of entering the country become more difficult, the cards could be utilized by groups like al Qaeda, particularly since we already have evidence that Middle Easterners are entering the United States through Mexico. (In October 2001, for example, an Iraqi-born smuggler named George Tajirian pled guilty to forging an alliance with a corrupt Mexican immigration officer, Angel Paramo, to smuggle over 1,000 illegal aliens from the Middle East into the United States across the southern border). Given that illegal entries of this kind do not create an administrative record of arrival, getting into the country in this way may become a particularly attractive option for
terrorists in the future.
The Successes
Of the 22 reforms in the visa tracking law that were to have been implemented by November 2003, nine were implemented on time and four others were implemented after the deadlines had passed. Again, we divide the most significant of these actions into three main categories: document fraud; information sharing; and admission/removal.
Document Fraud. Upon enactment of the visa tracking law, data on lost and stolen passports were required to be entered into the data system used to determine the admissibility or deportability of aliens. The purpose of this provision is to prevent aliens from using lost or stolen passports to gain entry into the United States fraudulently. While the administration did not begin tracking this data immediately upon enactment, the State Department (State) now has a system to automatically upload the numbers of lost and stolen passports into the Treasury Enforcement Communications System (TECS), which is used by immigration inspectors to determine the admissibility of aliens at U.S. ports of entry.
The administration also has complied with the provisions of the visa tracking law relating to a biometric technology standard. The Attorney General and State met the October 2002 deadline for the submission of a progress report to Congress on the establishment of a technology standard to verify the identity of non-citizens seeking entry. The Attorney General, State, and the National Institute of Standards and Technology (NIST) submitted by the November 2002 deadline a report on actions and resources necessary to create biometric machine-readable travel documents for non-citizens. The final report was not submitted by the deadline, however, because of delays at the Office of Management and Budget. The Attorney General and State also met the January 2003 deadline for certifying the biometric technology standard for verifying the identity of non-citizens seeking entry. These agencies recommended and certified fingerprints as the standard biometric identifier because fingerprint verification has a higher accuracy rate than facial recognition technology and because testing of iris recognition technology is incomplete. From a purely practical standpoint, the use of fingerprints to verify the identity of aliens makes the most sense in any case, since law enforcement agencies have been using fingerprints for years and the technology is widespread.
Information Sharing. While progress on the development of Chimera has stalled, the Administration has made some significant strides in improving information sharing among federal agencies. The visa tracking law required President Bush to report to Congress by September 2002 on the informational needs of DHS and State. The deadline was missed, but the President’s report was submitted in March 2003.3 In addition, an interim data-sharing system has been implemented to facilitate the exchange of information among federal immigration, law enforcement, and intelligence agencies regarding non-citizens until the Chimera system is developed. The interim system is not nearly as comprehensive as Chimera is supposed to be, but it does facilitate information flows between agencies. This information flow is critical to ensure that consular officers issuing visas and immigration inspectors determining admissibility have access to all available data regarding an alien’s criminal record and potential terrorist ties.
Other administration successes in the area of information sharing include: the timely submission to State by the Attorney General of a list of all U.S. educational institutions authorized to receive F or M nonimmigrant student visa holders; and the implementation of a system to ensure that no student visas (F, J, or M visas) are issued unless State has received electronic evidence from an approved U.S. institution of the alien’s acceptance and a consular officer has reviewed the alien’s visa record.
Admission/Removal. The certification of fingerprints as the biometric technology standard to verify identity deserves to be noted as a success in the admission/removal area, as well as the document fraud area listed above. It is an important accomplishment because the only way to truly identify an individual and reduce the use of fraudulent documents, aliases, and stolen identities is through a personal biometric identifier that is unique to every individual. By requiring the certification of a standard identifier that all law enforcement agencies will use, the visa tracking law makes it much less likely that a known or suspected terrorist, a criminal alien, or any alien who has been apprehended for illegal entry or other immigration violations will be able to use counterfeit or stolen documents to gain admission to the United States.
The implementation by the January 30, 2003, deadline of the Student and Exchange Visitor Information System (SEVIS) also is a noteworthy accomplishment of the Administration. Under SEVIS, approved U.S. educational institutions transmit electronically to State documentation of acceptance by the institution of a foreign student. State then reviews the student’s visa application and, if appropriate, issues an F, J, or M visa, depending on the type of program the student seeks to attend, and notifies DHS that the visa has been issued. Once the foreign student is admitted to the United States by an immigration inspector, DHS notifies the educational institution that the student is in the country. If the student fails to enroll or to commence classes, the educational institution is required to notify DHS.
The abuse of student visas by aliens seeking to remain permanently in the United States is nothing new. The General Accounting Office has been warning Congress about violations of student visas since at least 1975.4 Congress failed to act, however, until after the 1993 World Trade Center bombing, when it was discovered that Eyad Ismoil, the driver of the van filled with explosives, had entered the United States on a student visa, dropped out of school after three semesters, and remained here illegally to plot the attack. Spurred by this finding, Congress included in the 1996 IIRIRA a provision requiring the Attorney General, State, and the Department of Education to collect and maintain electronically-stored information on aliens granted F, J, and M student visas to determine whether they were complying with the terms of their visas. The program that resulted from that provision, the Coordinated Interagency Partnership Regulating International Students (CIPRIS), had not yet been fully implemented by September 2001.
When it was discovered that two of the September 11th hijackers, Mohammed Atta and Marwan al Shehhi, had fraudulently applied to change their status from tourists to students in order to extend their stay in the United States, Congress recognized the need include in the visa tracking law provisions to force full implementation of the student tracking system and to require additional data collection and notification requirements. As a result, CIPRIS evolved into the more detailed and expansive SEVIS.
Upcoming Deadlines
The implementation deadlines for the various reforms included in the visa tracking law range from May 14, 2002, (the date of enactment) to September 30, 2006. The most important of the upcoming deadlines is October 26, 2004. By that date, the law requires:
1) that all travel and entry documents issued by the United States to non-citizens include biometric identifiers and are machine readable;
2) that machines that can read both the standard and the biometric data on these cards are installed at all U.S. ports of entry; and
3) that, in order to participate in the visa waiver program, countries must issue their nationals machine-readable passports that include fingerprints.
Also upcoming are the implementation deadlines for the entry-exit system. The 1996 IIRIRA, not the visa tracking law, requires the creation of an automated system to track the entry and departure of all non-immigrant visitors to the United States, and the Immigration and Naturalization Service Data Management Improvement Act of 2000 establishes staggered deadlines for implementation of the entry-exit system. This latter law requires an automated system for matching entry and exit records of non-immigrants to be in place at all airports and seaports by December 31, 2003, at the 50 land ports with the highest volume of traffic by December 31, 2004, and at all other ports of entry by December 31, 2005. While the visa tracking law does not directly address these deadlines, it does affect the creation of the entry-exit system, thus making the deadlines noteworthy. The visa tracking law requires:
1) that the automated system utilize the certified biometric technology standard (i.e., fingerprints);
2) that the underlying database contains the arrival and departure data from machine-readable visas, passports, and other travel and entry documents; and
3) that all security databases relevant to determinations of admissibility be made interoperable.
The National Security Entry-Exit Registration System (NSEERS) represented the first step toward the creation of an entry-exit system. NSEERS required all males aged 16 or older from any of 25 countries designated as sponsors of terrorism or of "special interest" to be photographed and fingerprinted upon application for admission as non-immigrants at U.S. ports of entry. Foreign students seeking admission at a port of entry also were photographed and fingerprinted under NSEERS, regardless of their nationality. Furthermore, NSEERS required males aged 16 or older from these same countries who already were in the United States on non-immigrant visas to register in person at an INS office. Finally, NSEERS required all of these same non-immigrants to complete a departure check when they leave the United States, so that there is a record of their departure. Of the 83,000 non-immigrants already living in the United States who were required to register, some 14,000 appeared to be in violation of U.S. immigration laws, another 143 were arrested on criminal charges, and 11 were found to have terrorist connections. However, DHS announced on December 1, 2003 that it was suspending the requirement that non-immigrant males from the 25 countries periodically re-register during their stay in the United States.
The United States Visitor and Immigrant Status Indicator Technology (US VISIT) program is the second step toward a comprehensive, automated entry-exit system. Under the US VISIT system, all non-immigrant visa holders will be photographed and fingerprinted at a U.S. port of entry, regardless of their nationality. They also will be required to "check out" prior to leaving the country by scanning their visa or passport and placing their fingers on a fingerprint reader. DHS expects to have the entry portion of US VISIT implemented at airports and seaports by January 5, 2004, five days after the deadline set by Congress. It expects to phase in the exit portion of the system at airports and seaports over the next year. At this time, DHS does not have a clear plan for implementing US VISIT at land ports, so it appears doubtful that it will meet the December 2004 deadline.
For a list of all the deadlines in the visa tracking law, see
www.NumbersUSA.com/hottopic/deadlines.htm. For a comprehensive discussion of the provisions in the law, including pending deadlines, see www.cis.org/sites/cis.org/files/articles/2002/back502.html.
Conclusion
The Enhanced Border Security and Visa Entry Reform Act of 2002, if fully implemented, will significantly improve the security of our visa process through: 1) the use of biometric identifiers for all non-citizens; 2) access by DHS, State, the FBI, and the CIA to an integrated data system containing all available information on aliens that is relevant to determining admissibility; and 3) the matching of entry and departure information for all non-immigrants in a comprehensive entry-exit system.
These measures will not only reduce our vulnerability to terrorist attacks, but they also will deter illegal immigration by making it more difficult for aliens to overstay non-immigrant visas or to use stolen or counterfeited documents to obtain immigration benefits. Full implementation of the visa tracking law also will send a clear message that the United States intends to begin enforcing its immigration laws and closing the loopholes that have allowed terrorists, criminals, and illegal aliens to enter at will and remain as long as they choose. It is important to remember that, as long as any alien who is seeking a job or better opportunities is able to come to the United States illegally or remain here illegally after his visa expires, so too can any terrorist.
The Bush Administration has taken significant strides toward securing our homeland by implementing some of the provisions of the visa tracking law, and it deserves credit for those accomplishments. The fact that the Administration has failed to meet more than half of the deadlines that have passed so far, however, indicates a disturbing lack of commitment on the part of the Administration to secure our homeland from those who wish us harm and to uphold its Constitutional duty to ensure that the laws of the United States are faithfully executed.
Congress, having enacted the Enhanced Border Security and Visa Entry Reform Act, has a continuing duty to oversee its execution by the Administration. Rigorous congressional oversight serves a dual purpose: 1) to send the Administration — and the public — the message that Congress recognizes the importance of strict enforcement of U.S. immigration laws; and 2) to hold the Administration accountable for meeting the deadlines set out in the law and for implementing the law in the way Congress intended.
The security of the nation requires a commitment by both the White House and the Congress. The visa tracking law, insofar as it has been implemented, represents a positive step forward, but there is much left to do and the cost of failure could be extraordinarily high.
Endnotes
1 A detailed analysis of the Act is available in a previous Center for Immigration Studies Backgrounder entitled "The Enhanced Border Security and Visa Entry Reform Act of 2002: A Summary of H.R. 3525" and is available online at www.cis.org/sites/cis.org/files/articles/2002/back502.html
2 The entire CIS paper, The Open Door: How Militant Islamic Terrorists Entered and Remained in the United States, 1993-2001, is available online at
www.cis.org/sites/cis.org/files/articles/2002/terrorpr.html
3 A summary of the report, along with the President’s cover letter, may be found online at http://usinfo.state.gov/topical/pol/terror/03032626.htm
4 GGD-75-9, Better Controls Needed to Prevent Foreign Students from Violating the Conditions of Their Entry and Stay While In the United States. February 4, 1975.
http://161.203.16.4/f0302/095063.pdf
This is a joint publication with NumbersUSA Education and Research Foundation. Rosemary Jenks, J.D., is Director of Government Relations at NumbersUSA.com. Steven A. Camarota, Ph.D., is Director of Research at the Center for Immigration Studies.
